The scenario is two networks on the OPNsense side, one on the Sonicwall’s. Changing the defaults for a little bit of security. Both sides also have static IPs but this setup also worked when the OPNsense’s was dynamic.
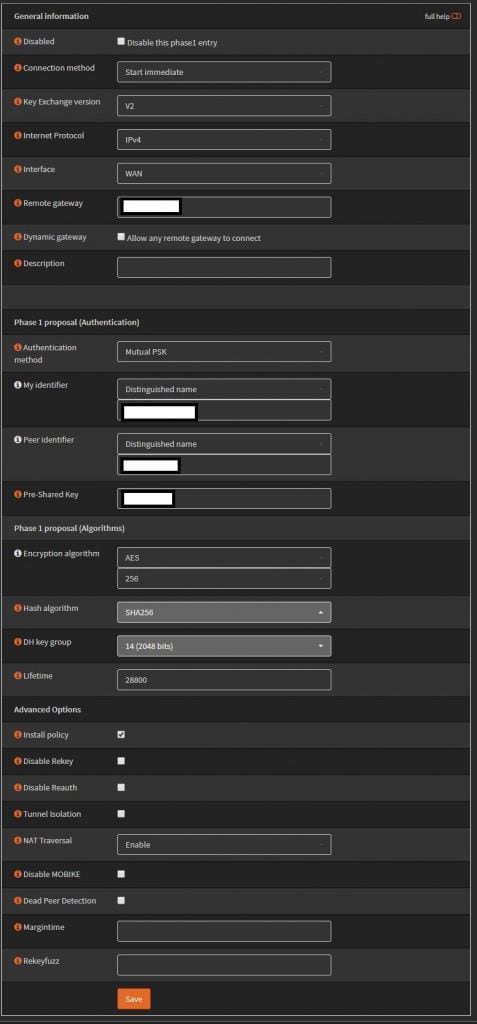
Using IKEv2 with preshared key. AES256, SHA256, and DH Group 14. For the identifiers use distinguished name, and enter in your domain names, these actually don’t have to resolve so you can make them up. Set life time to 28800.
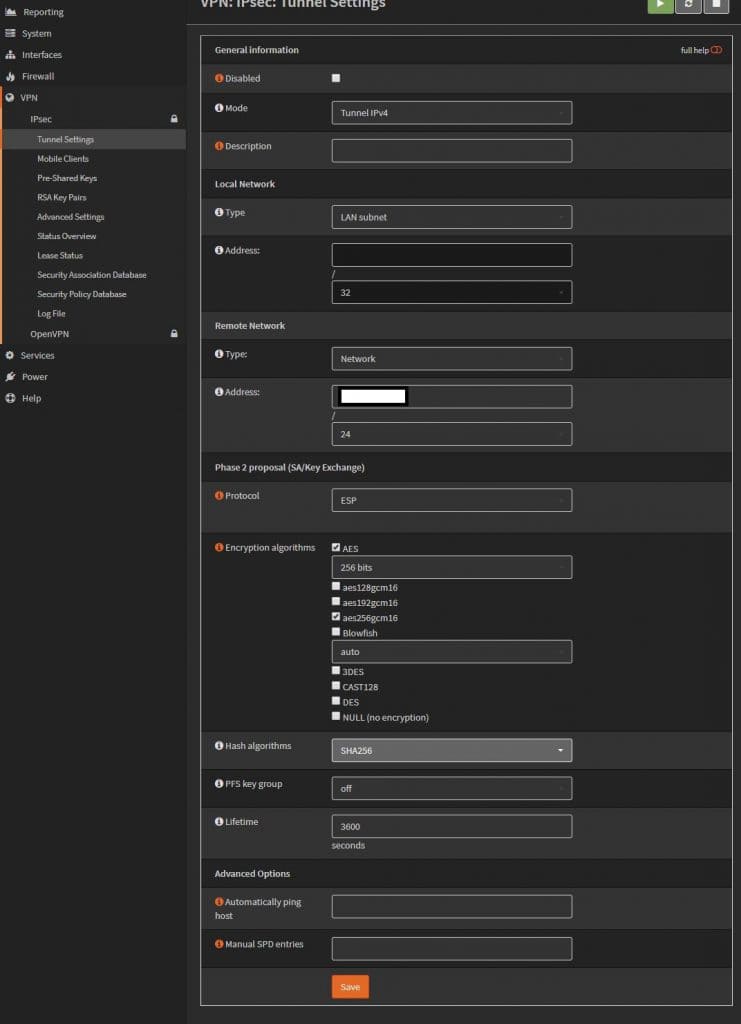
Phase 2. The remote network is going to be the Sonicwall’s “LAN” 192.168.x.0. Change the lifetime to 3600, uncheck unused ciphers. I have two networks on this side, so I just created another phase 2 policy for the 2nd network.
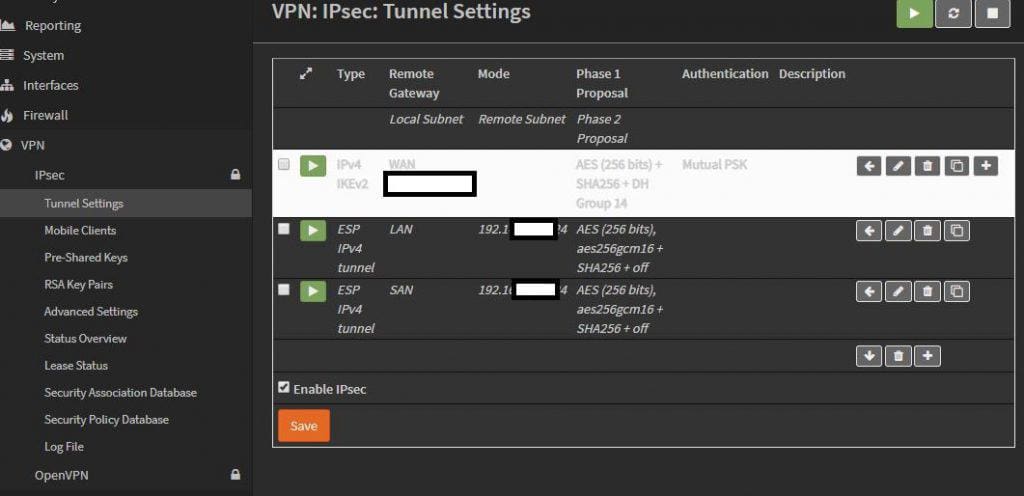
On the Sonicwall, enter in the OPNsense’s public IP, and the preshared key. For IKE IDs, these will be the My and Peer identifiers from phase 1 of the OPNsense config.
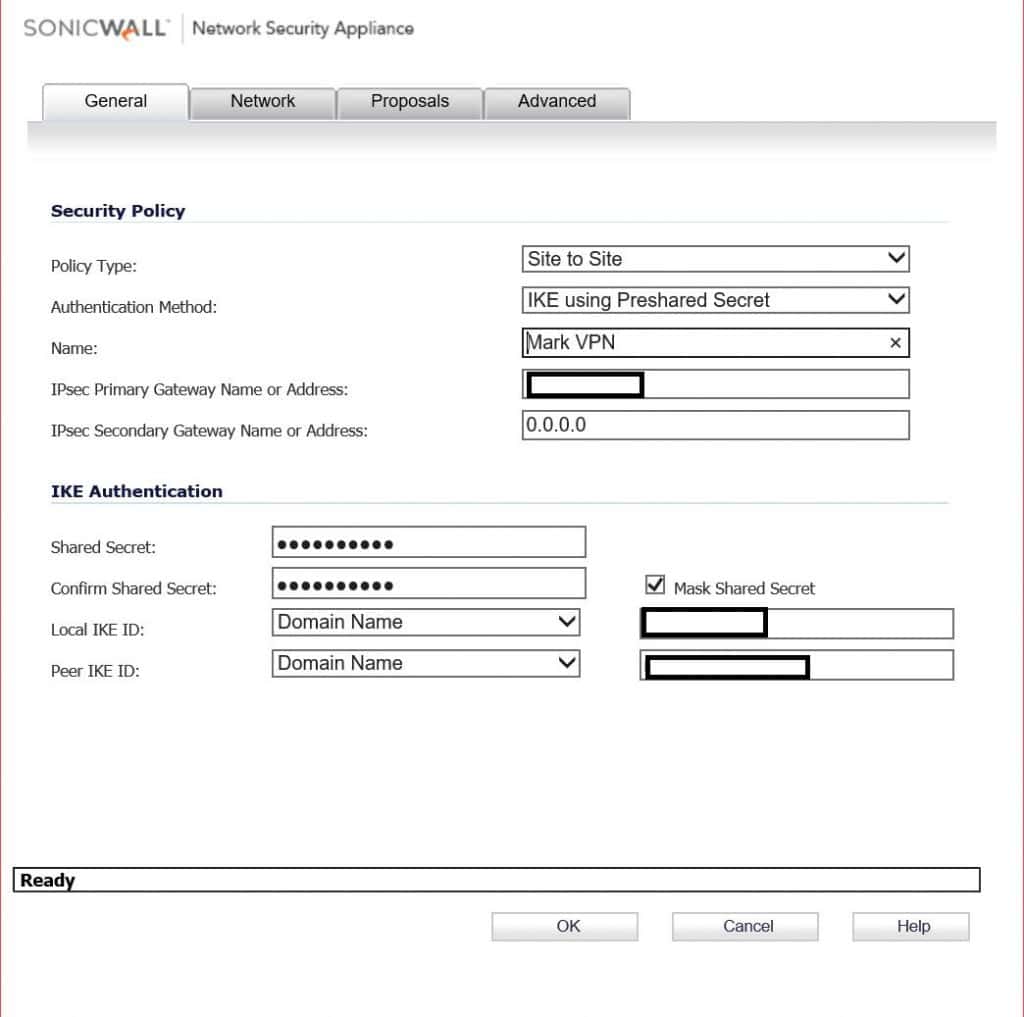
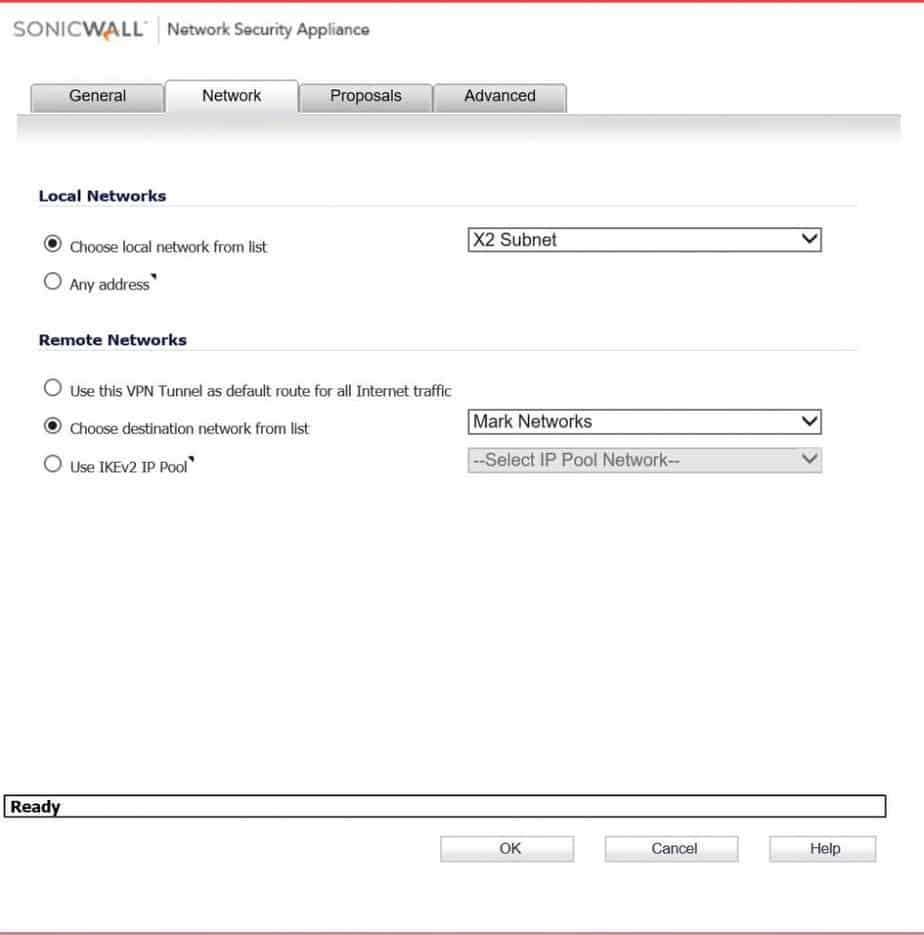
Pick the local network on the sonicwall side. For remote network pick the address object you should have created for this. ( Sorry, I don’t go over creating one of those). In this scenario there are two networks on the OPNsense side, so I create two VPN Network address objects, and put them in a group.
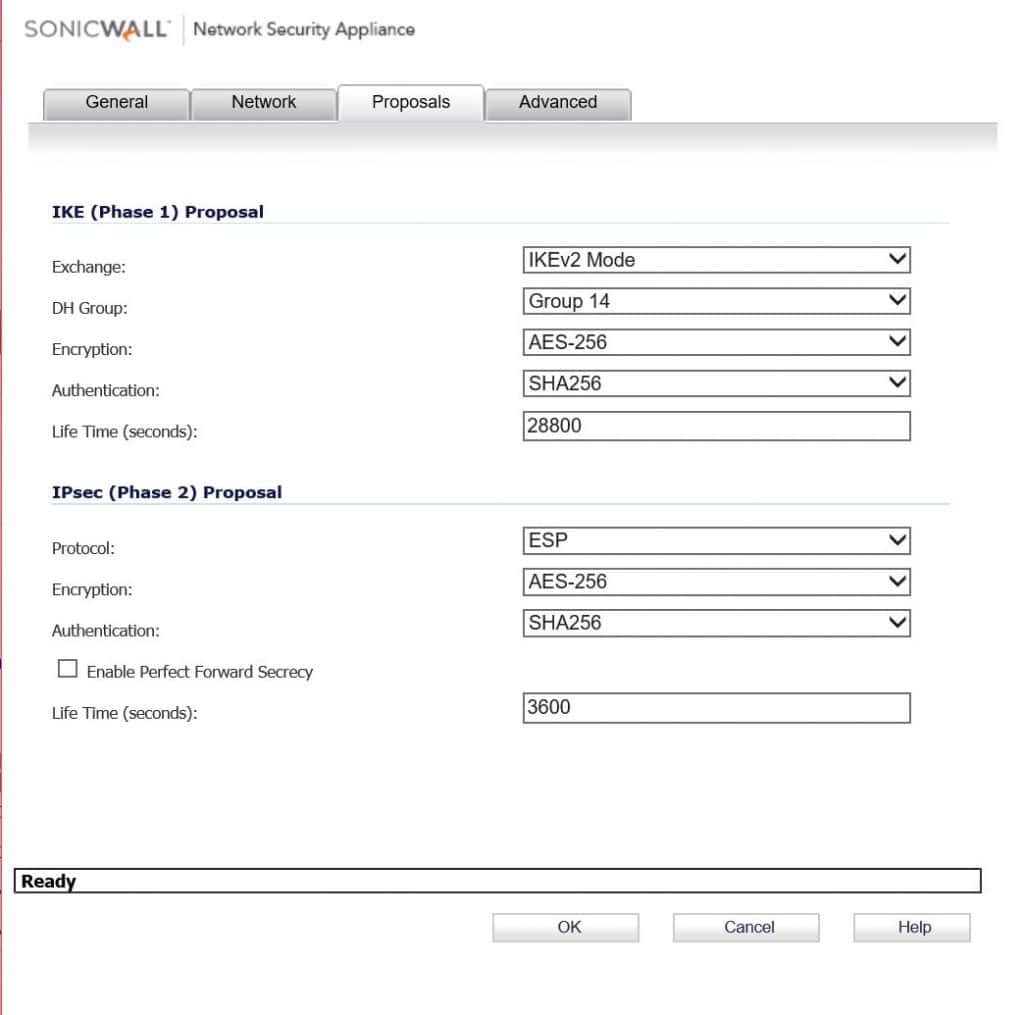
Here again using IKEv2 AES256, SHA256, and DH Group 14. Change Phase 2 life time to 3600.
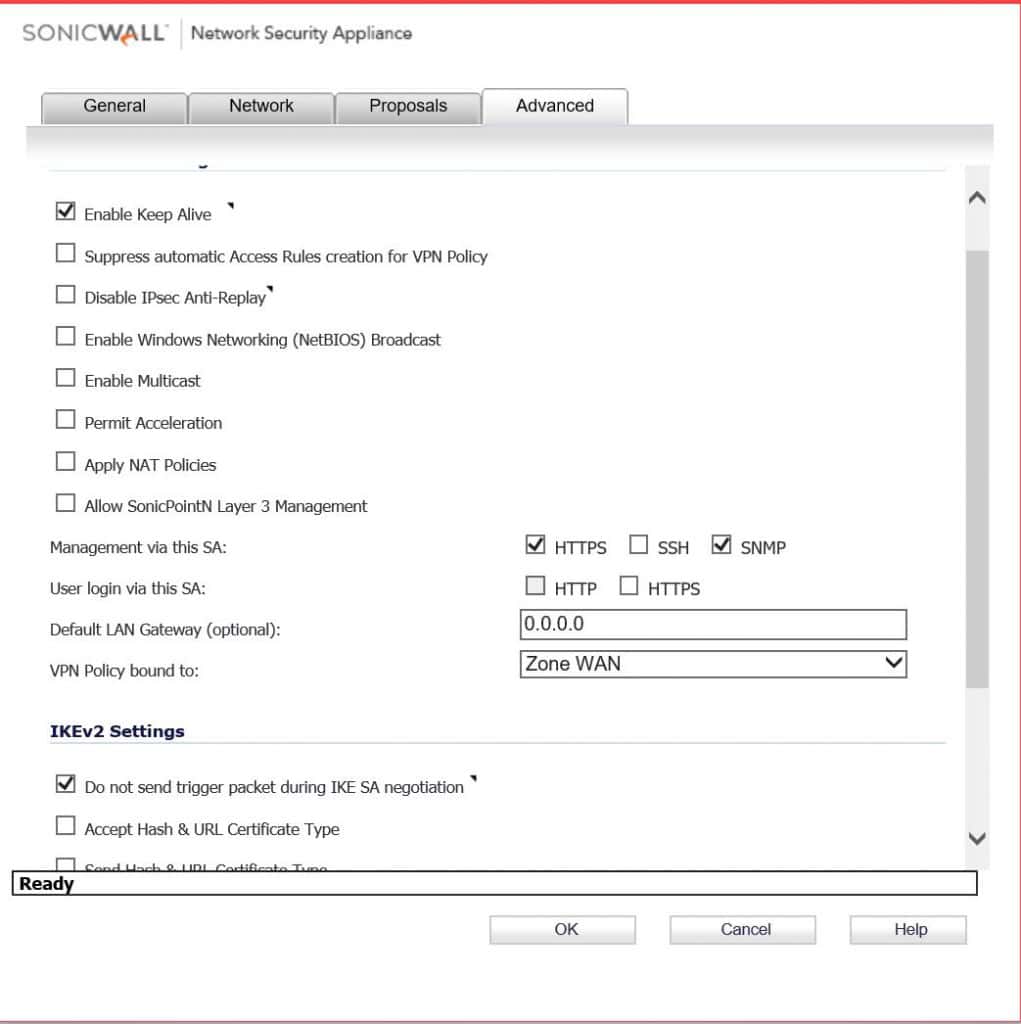
Enable keep alive and do not send trigger packet. Click OK and if everything goes well you should see some green lights. This also doesn’t go over what firewall rules you would need to create to pass traffic, you could do any any allow all, but you might no trust the other side.